Subdomain Takeover Explained 🏴 (And How Hackers Earn $$$ From It)
Subdomain Takeover Explained 🏴 (And How Hackers Earn $$$ From It)
Hey 👋,
If you’ve been around the bug bounty or cybersecurity space, you’ve probably heard of “Subdomain Takeover”. It sounds like something straight out of a hacker movie 🎬, but it’s very real — and one of the most lucrative bugs for security researchers.
In this guide, I’ll walk you through:
✅ What Subdomain Takeover is
✅ Why it’s dangerous
✅ Step-by-step guide with commands & tools
✅ GitHub repos you can use
✅ How companies can prevent it
By the end, you’ll know exactly how researchers detect and report these vulnerabilities (and why they get paid $$$ for it 💰).
🌍 What is Subdomain Takeover?
A subdomain takeover occurs when:
A company sets up a subdomain like
blog.example.com.That subdomain points to a third-party service (GitHub Pages, AWS S3, Heroku, etc.).
The company stops using that service but forgets to delete the DNS record.
Result: the subdomain points to an unclaimed resource.
Hackers can then register that resource and fully control the subdomain 🎯.
⚠️ Why is it Dangerous?
If an attacker takes over a subdomain, they can:
🎭 Host phishing pages under the company’s trusted domain
🦠 Spread malware or exploits
🔴 Damage brand reputation
🪄 Trick users into giving away credentials
That’s why organizations treat it as a high-impact vulnerability.
🔄 Visual Flow of Subdomain Takeover
Here’s a diagram to help you understand the process:
Company Domain → blog.example.com
↓
CNAME record
↓
Points to service (e.g., GitHub Pages, AWS, Heroku)
↓
Service is deleted / unclaimed ❌
↓
Hacker claims the service ✅
↓
Hacker controls blog.example.com 🏴🔍 Step-by-Step: Finding Subdomain Takeover
Here’s how researchers (for ethical hacking purposes only ⚠️) typically approach it:
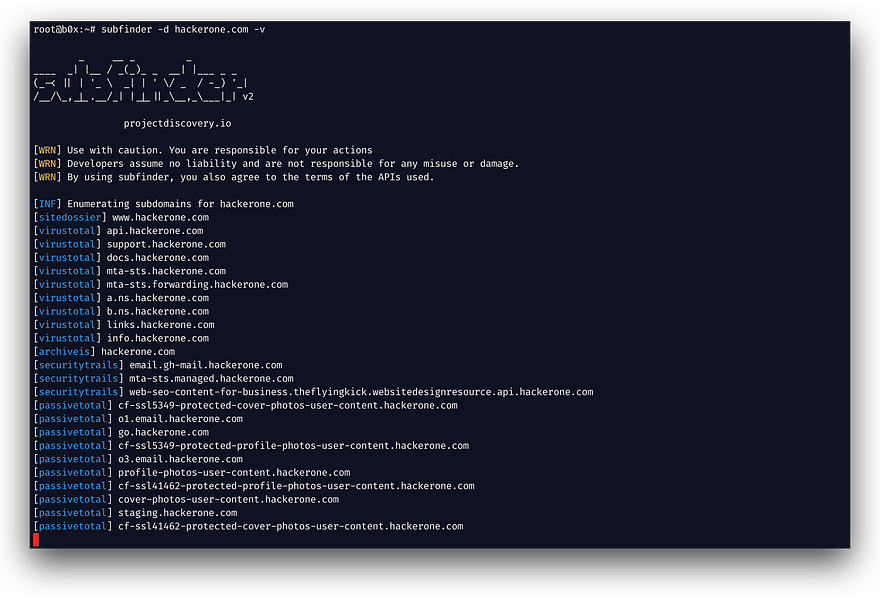
Step 1: Enumerate Subdomains
First, gather subdomains of the target.
Tools:
Command:
subfinder -d example.com -o subdomains.txt
Step 2: Check for CNAME Records
Look for subdomains pointing to external services.
Command (dig):
dig blog.example.comExample output:
blog.example.com. CNAME username.github.io.If username is unregistered → possible takeover 🚨.
Step 3: Detect Vulnerable Subdomains
Automate detection with dedicated tools.
Tools:
Command (Subjack):
subjack -w subdomains.txt -t 100 -timeout 30 -o results.txt -sslStep 4: Attempt Registration (Proof-of-Concept Only)
If available, register the resource to claim the subdomain.
Example:
If blog.example.com → username.github.io, and username is free, register that GitHub username.
⚠️ Only do this for responsible disclosure / bug bounty. Never host malicious content.
🛠️ GitHub Tools for Subdomain Takeover
🔎 Subjack → Detect subdomain takeover vulnerabilities.
⚡ SubOver → Fast detection across services.
🛡️ Nuclei Templates → Ready-to-use detection scripts.
🚀 Takeover → Simple automation tool.
📘 Can I Take Over XYZ → List of vulnerable services.
🛡️ How Companies Can Prevent It
🧹 Remove unused DNS records (dangling CNAMEs).
🔍 Run regular DNS audits.
📊 Monitor third-party service usage.
🤝 Launch bug bounty programs to catch issues early.
🎯 Final Thoughts
Subdomain takeovers are:
⚡ Easy to detect (with automation)
🔴 High in impact
🏴 A common source of bug bounty $$$
If you’re hunting bugs → learn Subfinder + Subjack + SubOver.
If you’re defending a company → audit DNS records today.
👋 Stay Connected
If you enjoyed this guide and want more practical tutorials, recon checklists, and hacker strategies, stay in touch:
📬 FREE Newsletter: thehackerslog.substack.com
📸 Twitter (X): @VipulSonule
🧑💼 LinkedIn: Vipul Sonule
✍️ Medium: Vipul Sonule