🤖 How to Use AI to Learn Bug Hunting & Cybersecurity Like a Pro (in 2025)
Hey there 👋,I’m Vipul, the mind behind The Hacker’s Log — where I break down the hacker’s mindset, tools, and secrets 🧠💻
Hey there 👋,
I’m Vipul, the mind behind The Hacker’s Log — where I break down the hacker’s mindset, tools, and secrets 🧠💻
Today, let’s talk about something that’s completely changing how we learn cybersecurity and bug hunting — AI.
Whether you’re a beginner trying to understand how XSS works or an advanced pentester looking to automate recon, AI can be your ultimate hacking buddy ⚡
Let’s dive in 👇
🔧 Download The Best AI Tools Pack (80+ tools) — perfect for automating, writing, and research.
🧭 Get The Hacker’s Recon Guide — a step-by-step playbook for discovering hidden subdomains, directories, and more.
🧠 Why AI Is a Game-Changer for Bug Hunters
Learning cybersecurity used to mean spending hours reading docs, watching long tutorials, and testing tools manually.
Now, with AI tools, you can:
Learn faster with personalized guidance 🤝
Practice with real-world labs 🧑💻
Automate recon, exploit generation, and report writing
Get instant explanations for vulnerabilities
AI isn’t replacing hackers — it’s supercharging us ⚙️💥
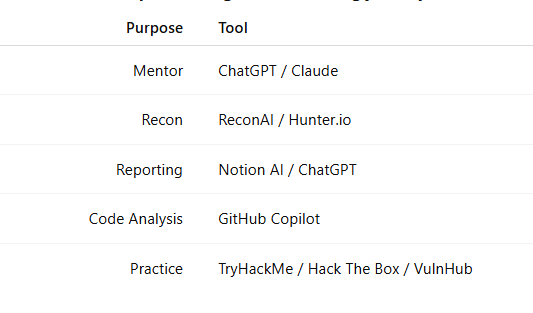
🧩 Step 1: Use AI as Your Personal Mentor
Forget boring tutorials. Use AI chatbots to simulate a mentor who explains, guides, and challenges you.
Try these 👇
🧠 ChatGPT — Ask it to explain CVEs, write Burp Suite macros, or simulate vulnerable websites.
🤖 Perplexity AI — Great for research and gathering sources.
💬 Claude AI — Ideal for long bug bounty write-ups or analyzing HTTP responses.
💡 Prompt idea:
“You are a cybersecurity mentor. Explain how to find IDOR vulnerabilities with practical examples and Burp Suite tips.”
You’ll be surprised how deep these AI models can go when you prompt them like a mentor.
🔍 Step 2: Automate Recon & Data Collection with AI Tools
Recon is the most time-consuming part of bug hunting. AI can help you automate repetitive tasks while you focus on analysis.
Tools to Explore:
🛰️ ReconAI — Uses AI to scan subdomains and detect patterns.
🕵️ AIxploit — AI-assisted vulnerability scanning and exploit generation.
🧾 Burp Suite + AI workflows — Summarizes intercepted requests and helps you detect issues faster.
🌐 Hunter.io — Combine it with AI to find email leaks and attack surfaces.
💡 Bonus Tip: Use Python scripts with the OpenAI API to automate tasks like pattern detection or URL classification.
Example starter snippet:
import openaiprompt = “Analyze this HTTP response and tell me if there’s a possible XSS or IDOR vulnerability:\n\n[Insert HTTP response]”
# Use this prompt pattern with the OpenAI API to get analysis suggestions.💣 Step 3: Learn by Doing — AI-Generated Labs
The best way to learn hacking is still hands-on.
But AI can make your lab learning 10x better:
🧪 TryHackMe — Use ChatGPT to guide you step-by-step through rooms.
🎯 Hack The Box — Use AI to help analyze machine hints without spoilers.
🧰 VulnHub — Generate summarized walkthroughs using AI to check your understanding.
💡 Example prompt:
“Explain how to escalate privileges on the ‘RootMe’ machine from TryHackMe using Linux misconfigurations.”
You’ll get a learning path customized for your understanding level.
🧰 Step 4: Master Reporting & Documentation with AI
Every great hacker knows — a good report gets rewarded 💸
AI can help you:
Write professional bug bounty reports 🧾
Generate proof-of-concept (PoC) markdowns
Summarize scope and impact clearly for triage teams
Translate technical findings into client-friendly language
Try:
🖋️ Notion AI — Create structured reports.
📝 ChatGPT — Polish and expand technical sections.
🧑💼 Grammarly — Clean up tone and presentation.
💡 Prompt idea:
“Write a detailed bug bounty report for an XSS vulnerability with impact, reproduction steps, and mitigation advice.”
📸 Visualize and Document Everything
People remember visuals more than text — especially in bug bounty reports or blogs.
Use tools like:
🎨 Excalidraw — Draw recon maps.
📊 Mermaid Live Editor — Create flowcharts of attack paths.
📸 Carbon — Turn your code snippets into beautiful images for blog posts.
(Example image idea: a flowchart showing Recon → AI Analysis → Exploit → Report)
🚀 Step 5: Build Your Own AI + Cyber Toolkit
Here’s a small stack to start your AI-augmented hacking journey:
🧠 80+ AI Tools Vault 2025 — The Ultimate Collection
Unlock the future of productivity with 80+ handpicked AI tools that hackers, developers, and creators use daily.
From recon automation to AI-assisted learning — this vault is your secret weapon ⚡
🧰 Grab it here → AI Tools Vault 2025
📘 Bonus: Hacker’s Recon Guide
Want to master reconnaissance and OSINT like a pro?
This Recon Guide is a field-tested resource that teaches you every stage — from subdomain hunting to endpoint discovery.
🕵️♂️ Get it here → The Hacker’s Recon Guide
🌍 The Future: AI + Hackers = Cyber Guardians
AI won’t replace ethical hackers — it’ll empower them.
In 2025 and beyond, companies will want AI-assisted pentesters who can find vulnerabilities faster and explain them clearly.
If you learn to combine AI reasoning + hacking logic, you’ll be unstoppable. ⚔️
📚 Related Reads (From My Blog Series)
Hidden API Endpoints: The Hacker’s Secret Weapon 🔍
I’m a cybersecurity enthusiast and the writer behind The Hacker’s Log — where I break down how real hackers think…infosecwriteups.com
The Secret Life of Subdomains 🌐: From Takeover to $$$ Bounties
When most people think of a website, they imagine the main domain: example.com. But hackers know the real treasure…infosecwriteups.com
How Hackers Use AI to Find Vulnerabilities Faster 🤖🔓
“99% of websites have security issues. Most developers don’t even know it.”infosecwriteups.com
✉️ Join The Hacker’s Log Community
I regularly share posts on:
🔍 Recon secrets
🧩 Exploit techniques
🧠 AI tools for hackers
💰 Bug bounty insights
Follow for weekly drops 💡
📌 Connect With The Hacker’s Log
If you enjoyed this guide, join our growing ethical hacking community for advanced tutorials, case studies, and recon challenges!
🌐 Website:
https://thehackerslog.com/
📰 Substack:
🛒 Recon Guide: https://thehackerslog.gumroad.com/l/hackersreconguide
✍️ Medium: https://medium.com/@vipulsonule71
🔗 LinkedIn: The Hacker’s Log
Happy Hunting — and always, hack ethically. ⚔️