0-Day Hunting Guide 🕵️♂️: Recon Techniques Nobody Talks About
Hey there, hacker 👋 — Vipul here from The Hacker’s Log.
If you think 0-day hunting is only for elite hackers, let me stop you right here.
It’s not.
It’s for patient hackers — the ones who dig deeper, observe silently, and find what the world missed.
Today, I’m giving you the real recon techniques nobody actually talks about publicly.
Not theory.
Not boring definitions.
But street-level hacker recon you can apply today — the stuff I wish someone had taught me years ago.
Get ready for:
✔ hidden recon sources
✔ dirty OSINT tricks
✔ GitHub leaks sniffing
✔ 0-day-style fingerprinting
✔ real-world case studies
✔ tools + commands
✔ ASCII diagrams + visuals
✔ tables comparing recon methods
Let’s dive in 🕶️🔥
📘 Hacker’s Recon Guide — Master the art of recon. Find hidden endpoints and sensitive data like a pro.
🚀 The Ultimate Hacker’s Toolkit (All-in-One Bundle)-All my best-selling hacking & AI resources, packed together to supercharge your recon, automation, and bug-hunting workflow
🔥 Hidden API Endpoints: The Hacker’s Secret Weapon — A full playbook on how I discover, analyze, and exploit private APIs.
🤖 AI Prompts for Bug Hunters — 100+ ready-to-use prompts for automating recon, crafting payloads, and analyzing responses with AI.
🧠 Best AI Tools for Hackers & Developers — A curated list of tools I personally use to make recon faster and reporting cleaner.
Mastering C++ Step by Step — A Practical Approach for Beginners
A vulnerability nobody has seen or reported — yet.
But how do hackers actually find them?
Through recon beyond recon — looking in places other bug hunters don’t even think about.
🎯 The Real Secret:
0-days don’t hide deep — they hide in blind spots.
Blind spots like:
Unlisted subdomains
Forgotten staging servers
Developer test endpoints
Hidden debug parameters
Leaked tokens inside commit history
Old JS files still served in production
Internal APIs exposed accidentally
Those aren’t protected by a firewall…
Those are protected by ignorance.
Let me show you how to reveal them 👇
🕵️ Chapter 2: The Forgotten Recon Techniques (Nobody Talks About)
These are the techniques that never appear in standard bug bounty courses.
But real hunters use them daily.
Technique #1 — Fingerprint the Entire Company, Not Just the Main Domain 🏢
Most hunters only attack:
target.comBut real 0-day hunters map the entire digital identity:
Product names
Acquired companies
Old domains
App stores
CDN assets
Cloud storage buckets
GitHub orgs
Android apps
iOS apps🔹 Visual Map
┌────────────┐
│ target.com │
└──────┬─────┘
│
┌───────────────┼────────────────┐
▼ ▼ ▼
old-staging.com api.target.com mobile-target.net
│ │ │
▼ ▼ ▼
forgotten dev exposed test unpublished API
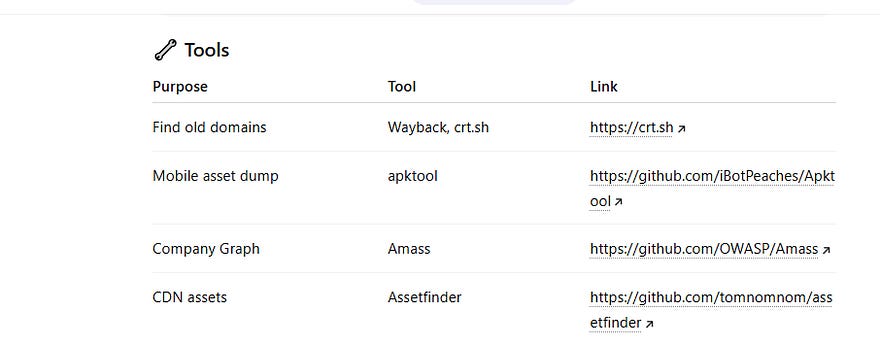
dashboard routes endpoints🔧 Tools
🧪 Real Example
Once found a banking company using an old domain from 2014 still pointing to an active S3 bucket.
Inside was:
/test/folderAPI keys
Internal endpoints
Dev credentials
A literal 0-day playground.
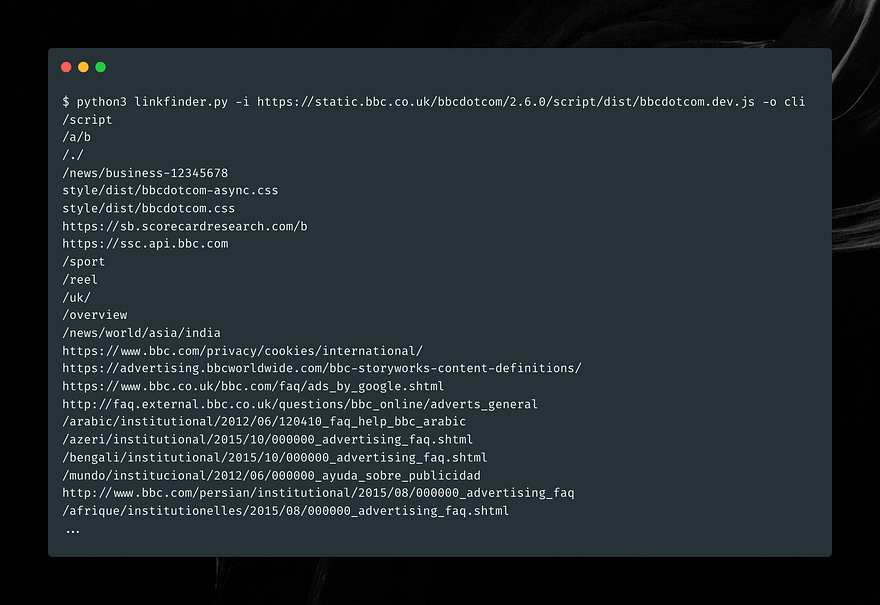
Technique #2 — Enumerate JavaScript: The Source Code Goldmine 🟨
Most hackers look at JS once.
0-day hunters look at it line by line.
What to extract:
hidden API endpoints
debug routes
secret tokens
environment variables
auth bypass parameters
CLI trick:
cat script.js | grep -Ei “key|secret|token|debug|internal”Tools
LinkFinder → https://github.com/GerbenJavado/LinkFinder
JSParser → https://github.com/nahamsec/JSParser
🔍 Case Study
A friend found a private internal API in a JS file that allowed:
?debug=true&env=stagingSwitching env exposed admin endpoints from the staging environment that were NOT authenticated.
Boom: 0-day.
Technique #3 — Target Backup Files (The Ultimate 0-Day Candy) 🍬
Most companies accidentally leak backups:
.zip.rar.old.bak.backup.swp
Try:
site.com/config.php.bak
site.com/index.php~Tools
Use dirsearch:
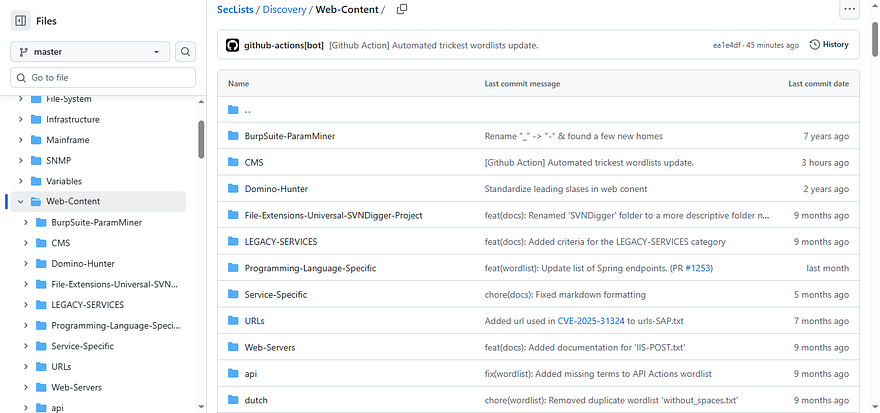
dirsearch -u https://target.com -w backups.txt -x 403,404GitHub wordlist for backups:
https://github.com/danielmiessler/SecLists/tree/master/Discovery/Web-Content
Real Story
Found db.sql.gz on a fintech domain.
It contained:
DB schema
Admin users
API secrets
Payment parameters
That was a full compromise, plain and simple.
Technique #4 — Search the Developer’s GitHub (Dirty OSINT) 🧑💻
This is a secret I rarely share.
Look for:
commits mentioning “fix later”
exposed tokens
internal URLs
test script
Firebase config
Slack tokens
AWS keys
CLI:
git log --all --grep=”key”Tools
Tool Use Case Link GitLeaks token leaks https://github.com/gitleaks/gitleaks GitHound org-wide OSINT https://github.com/tillson/git-hound TruffleHog deep secret scanning https://github.com/trufflesecurity/trufflehog
Real Example
A developer accidentally committed:
INTERNAL_API=https://dev-api.target.com/internal/v2This led to:
admin panel
user impersonation endpoints
zero authentication
A true 0-day.
Technique #5 — The API Swagger Trick 🧴
Search for undocumented swagger pages:
/swagger
/api/docs
/openapi.json
/openapi.yaml
/v2/api-docsOnce found, run:
?format=html
?deep=trueTools
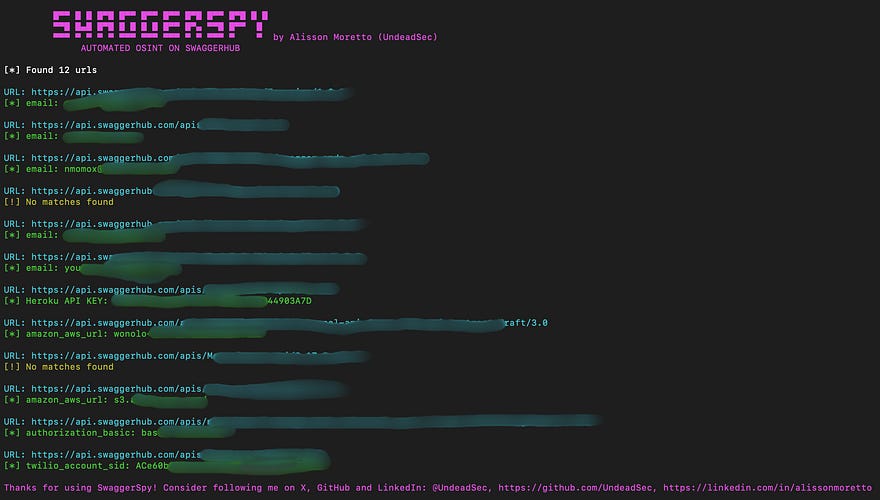
SwaggerSpy (underrated) → https://github.com/apisec-inc/swagger-spy
Postman for automatic generation
Why It Works
Swagger often documents endpoints that are NOT meant to be public.
Including experimental routes developers assume nobody will see.
Technique #6 — Full Mobile Recon: APK = 0-Day Generator 📱
Mobile apps leak:
Firebase URLs
API keys
Hidden environments
Debug endpoints
GraphQL paths
Extract APK data:
apktool d app.apk
grep -Ri “key” .
grep -Ri “dev” .Look for:
.plist.jsonconfigs.xmlexposed settings
🔥 I once found a hidden admin endpoint only referenced inside NetworkHelper.java.
Technique #7 — Brutal Parameter Fuzzing (The 0-Day Magnet) 🎣
Nobody fuzzes parameters deeply.
Everyone fuzzes endpoints.
But the 0-day magic is inside this:
/api/update?mode=dev
/api/login?debug=true
/api/upload?path=../../
/v2/data?format=xmlTools
Tool Strength Arjun discovers hidden parameters ParamSpider scans JS + HTML for parameters Kiterunner API brute-force
CLI Example
arjun -u https://target.com/api/profile📦 Chapter 3: 0-Day Recon Workflow (Vipul’s Full Framework)
Here’s my exact workflow combining Part 1 + Part 2 into a single powerful framework:
STEP 1 — Identity Recon (Company Fingerprinting)
Identify:
infrastructure
old domains
cloud assets
CDN buckets
mobile apps
open-source repos
Tools:
Amass, Assetfinder, CT logs
STEP 2 — Deep Subdomain Graph
Use multiple tools:
amass enum -brute -d target.com
subfinder -d target.com
assetfinder target.comMerge + sort:
cat *.txt | sort -u > hosts.txtScan live hosts:
httpx -l hosts.txt -o live.txtSTEP 3 — JS Endpoint Mining
python3 linkfinder.py -i https://target.com -o results.htmlSTEP 4 — Hidden API Discovery
Swagger
GraphQL introspection
Developer test endpoints
debug URLs
STEP 5 — Backup File Hunting
Search .bak .zip .rar .old.
STEP 6 — GitHub & Dev OSINT
Search employees + commits.
STEP 7 — Mobile Deep Dive
Reverse the APK.
Extract endpoints.
STEP 8 — Parameter Bruteforce
Use Arjun + Kiterunner.
STEP 9 — Attack Surface Diff (The Secret Sauce) 🧠
Compare:
Old JS vs new JS
Old endpoints vs new endpoints
Old subdomains vs new subdomains
You’d be shocked how many 0-days appear in the diff.
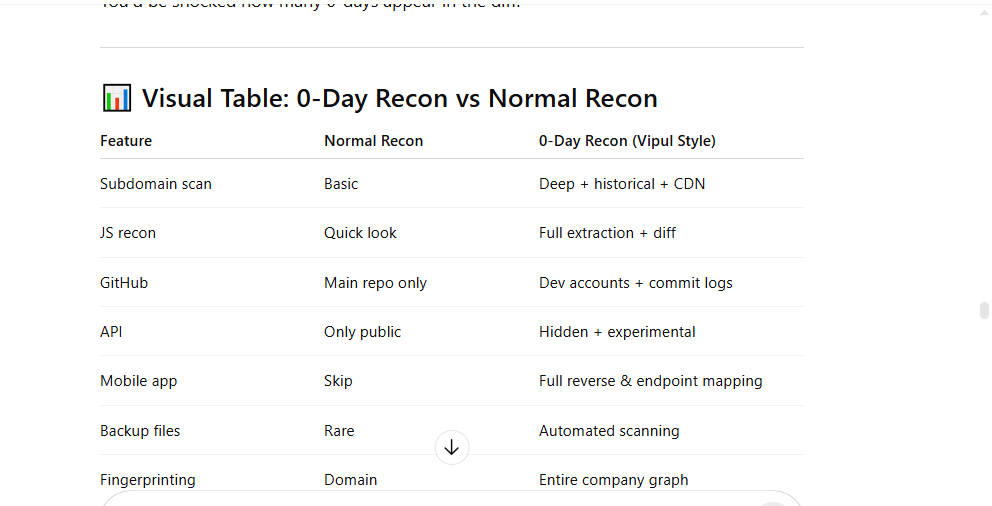
📊 Visual Table: 0-Day Recon vs Normal Recon
💣 Case Study: How One Hidden Staging Server Led to a 0-Day
A real-world example.
Step 1 — Found an old subdomain
staging-dashboard.old-target.net
Step 2 — It returned 403
Most hunters skipped.
But I probed it further:
curl -I -H “X-Forwarded-Host: admin” https://staging-dashboard.old-target.netResponse: 200 OK
CORS misconfig.
Step 3 — Extracted JS
Found:
/internal/v3/getUser
/internal/v3/deleteUserStep 4 — API not authenticated
Could delete any user.
Account takeover of all staging accounts.
This is 0-day recon:
Finding what nobody is looking at.
🧠 Advanced Trick: AI-Assisted 0-Day Hunting
Just like in my Medium story, AI can:
classify code smells
detect unusual API behavior
highlight suspicious JS
summarize GitHub commits
auto-generate recon maps
Example prompt I use:
Analyze this JavaScript for potential security issues, hidden endpoints, secrets, or unsafe API calls. Provide a human-readable summary.🗂️ Tools Mentioned
Tool Link
https://github.com/OWASP/Amass
https://github.com/tomnomnom/assetfinder https://github.com/projectdiscovery/subfinder https://github.com/projectdiscovery/httpx https://github.com/maurosoria/dirsearch
🧰 1. Ultimate Hacker’s Toolkit — 250+ Tools, Scripts & Automation Pack
A complete collection of:
Recon scripts
Bug bounty tools
OSINT workflows
Automation templates
Wordlists, payloads, and cheat sheets
Perfect for beginners and pros looking to speed up recon and reporting.
👉 Get it here:
https://thehackerslog.gumroad.com/l/ultimatetoolkit
🔍 2. Hidden API Endpoints Playbook — 50+ Techniques + Scripts
This guide reveals methods to extract:
Hidden internal APIs
Debug routes
Mobile-only endpoints
Experimental dev paths
Undocumented API behavior
Includes scripts + real-world examples.
👉 Download here:
https://thehackerslog.gumroad.com/l/hiddenapiendpoints
🤖 3. 500+ AI Prompts for Hackers, Creators & Developers
A collection of ultra-optimized prompts for:
Recon automation
Content creation
Coding assistance
Debugging
Security scanning
Bug hunting
Workflow speed-ups
👉 Get the prompt pack:
https://thehackerslog.gumroad.com/l/aiprompts
💻 4. Mastering C++ for Beginners — From Zero to Advanced
A complete C++ learning series:
Basics to OOP
Data structures
Memory management
Real coding exercises
Beginner-friendly explanations
Ideal for students, programmers, and security learners.
👉 Start learning:
https://thehackerslog.gumroad.com/l/masteringcppom/
🕵️♂️ 5. Hacker’s Recon Guide — Professional Recon in 2025
A deep-dive manual that teaches:
Modern recon
OSINT extraction
API discovery
Cloud asset mapping
JS analysis
0-day style scanning
One of your best products for serious bug hunters.
👉 Grab the guide:
https://thehackerslog.gumroad.com/l/hackersreconguide?
🚀 Recommended Tools to Boost Your Online Income (2025 Edition)
Whether you’re a cybersecurity professional, content creator, or someone trying to build automated income streams — these are tools I personally recommend for faster growth and hands-off systems.
🔥 1. AI Profit Sniper — Build Faceless Income Machines
AI Profit Sniper helps you:
Create faceless videos automatically
Auto-post content across platforms
Grow affiliate commissions even while you sleep
Build a passive content engine using AI
If you’ve ever dreamed of a set-and-forget income system, this is one of the best tools to try.
👉 Try AI Profit Sniper:
https://www.aiprofitsniper.com/dindex1.html#aff=vipulsonule
🎬 2. TubeMagic — Your AI-Powered YouTube Growth Assistant
Perfect for creators who want to scale fast. TubeMagic generates:
Video ideas
Scripts
Titles, tags, descriptions
Community posts
Auto SEO optimization
It works like having a full YouTube team powered by AI.
👉 Explore TubeMagic:
https://tubemagic.com/ds#aff=vipulsonule
🤖 3. AgentX — Deploy Thousands of AI Bots for Marketing
AgentX gives you a personal AI workforce capable of:
Creating content
Generating landing pages
Writing email sequences
Building marketing campaign
Automating entire digital businesses
Just give a command — AgentX does the rest.
👉 Get AgentX:
https://getagentx.com/order#aff=vipulsonule
🗂️ Tools Mentioned
GitHub - tillson/git-hound: Fast GitHub recon tool. Scans for leaked secrets across all of GitHub…
Fast GitHub recon tool. Scans for leaked secrets across all of GitHub, not just known repos and orgs. Support for…github.com
📌 Connect With Us
🌐 Website:
https://thehackerslog.com/
📝 Substack:
🔗 LinkedIn: The Hackers Log
✍️ Medium: @vipulsonule71




It's interesting how you consistently manage to dig into the unsaid parts of cybersecurity, making this recon guide feel as freash and useful as your AI prompts for bug hunters, and I'm totally ready to dive into these hidden sources.